

Blockchain Cryptography Simplified
In addition to being open-sourced and traceable, one of the reasons why this new genre of technology has erupted is because of how secure it is.
Every transaction or an event that occurs on the Blockchain is highly secure, encrypted and fast. While it looks very simple from the outside, the inside of a block is highly complicated, being just a bunch of data put together, a lot of crazy maths and algorithms run to keep it secure, thanks to Blockchain Cryptography.
Let’s understand it in detail.
Cryptography In General
Cryptography comes from the combination of two words: hidden (crypto) + writing (graphy); and its working can further be broken down into two major processes, Encryption and Decryption.
Whenever the data is sent via the P2P (point to point) network, it is first encrypted.
This means that the information is coded in such a way that no one can understand by looking at it.
After this ‘encrypted’ information reaches the other point (or node) it is decrypted, which means the data is decoded and now the data can be interpreted easily by the receiver.

What is Blockchain Cryptography?
The working of a Blockchain relies on three different technologies. Distributed ledger, Peer-to-peer network, and Cryptographic security.
The first and second technologies are important for conducting transactions on the Blockchain from one peer (person) to another and also validating them. It is the third (Cryptographic security) which ensures security.
In short, Cryptography in Blockchain is the method used to secure important data from a third party or access which is not authorised. Cryptography is a mandatory security protocol of any transaction and in the Blockchain network, it always secures the two nodes between whom the transaction is taking place.
Similar to messages sent on WhatsApp, it even encrypts the information so that no third party can identify the actual information.

It is also important to note that every Blockchain transaction has its own certificate and with the use of Cryptography there can be no transaction which takes place without a certificate.
These certificates (generated digitally) are also important in recognising the legitimacy of any transaction. The transaction on the Blockchain network issues a chain of certificates that are used to authenticate an entity.
The transaction chain begins with the certificate of that entity, and each certificate in the chain is signed by the entity and then identified by the next certificate in the chain. Fundamentally it is a chain of trust.
In Cryptography, users can also issue self-signed certificates. These certificates are public key certificates that a user or an entity issues on their own behalf. Even though there is a low trust value, these certificates are free and also easy to make.
The self-signed certificates bind the entity to the transaction and the transaction cannot proceed unless it is first signed by the users themselves.
Cryptographic Hash Functions
Now that we know what Blockchain Cryptography is, it is important to understand its application and how it functions exactly on the Blockchain. Every block in the Blockchain works on a “hash (#)” mechanism.
This mechanism is a function where the input can be anything: an alphabet, a number or any symbol. No matter whatever the input the output is always a hash (#) value.
Moreover, the hash is always of a fixed length no matter what the length of the input value is. Hashing is an important factor for securing the Blockchain and making it impenetrable.
Cryptographic hashing codes the information or data on Blockchain into an unreadable and unhackable text. Bitcoin for example uses the SHA256 (Secure Hash Algorithm 256-bit) for cryptographic security.
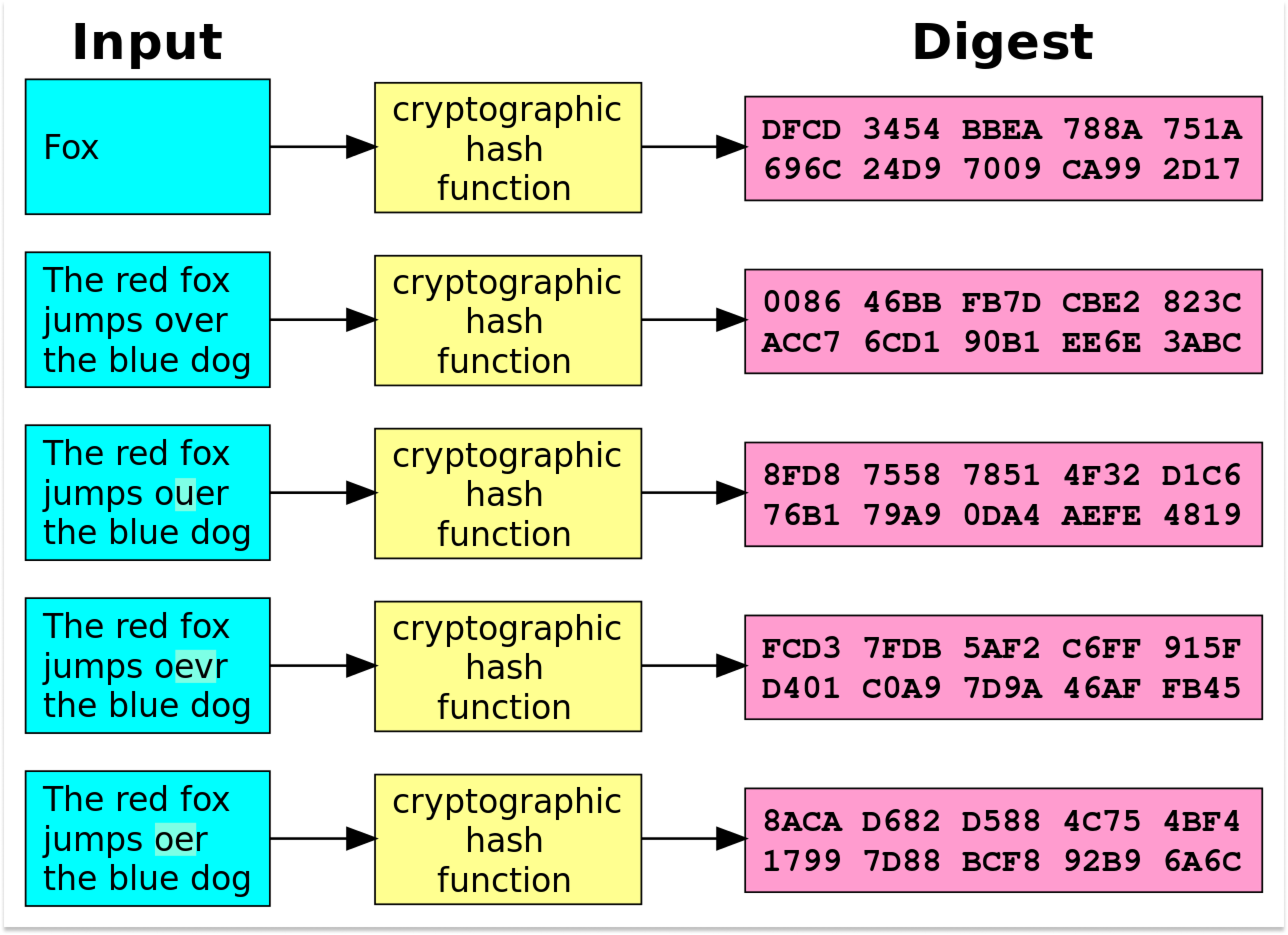
The number 256 in SHA256 implies 256 bits which is the number of zeros and ones which the algorithm can contain in the data. Since our computers are designed to read and interpret data in the binary (as ones and zeros) form.
The SHA256 mechanism is designed to provide that ease to our computers. A few characteristics of this algorithm are:
- Message Length: The size of the message should be within the limits of the algorithm for the generation of random values.
- Digest Length: The length of the hash digest should be 256 bits in SHA 256 algorithm. The higher the length value, the more time is taken for calculations along with increased cost.
- Irreversible: SHA 256 is irreversible by design. This means that once implemented the function cannot be reversed.
Working of SHA 256
Even though there is a lot of math happening inside the algorithm, the working of SHA 256 can be divided into five different segments:
- Padding Bits: It is the addition of extra bits to the message, such that the length is exactly 64 bits short of a multiple of 512.
- Padding Length: The 64 bits of data can now be added to make the final plaintext a multiple of 512.
- Initialising the Buffers: It requires the initialisation of default values for eight buffers to be used ahead. Eg. a = 0x6a09e667.
- Compression Functions: This is the breakdown of the complete message into multiple blocks of 512 bits each.
- Output: The final value received after the implementation of all the above steps. This output is then used as the input for the next block in the Blockchain. This also ensures the fact that the next block is always derived from the previous block.
Applications of SHA 256
Now that it is known in simple context how the algorithm functions. Let’s take a look at where we see SHA 256 being used:
- Digital Signature Verification: Digital signatures are required to verify the authenticity of a document or a transaction. SHA 256 has been ensuring such verifications for quite some time now.
- Password Hashing: Websites store user passwords in a hashed format for two reasons. It helps in ensuring a sense of privacy, and it makes the load on the central database lesser as all the data is of similar size.
- SSL Handshake: The SSL handshake consists of web browsers and web servers agreeing on encryption keys and hashing authentication to prepare a secure connection. This entire process is made possible because of SHA 256
- Integrity Checks: SHA 256 helps in maintaining the full value functionality of files and ensures no tampering takes place by an unauthorised entity.
In conclusion, the new technology of Blockchain Cryptography is a revolution under development. It definitely comes with its own risks and as time passes more and more improvements are being made to make the Blockchain faster and even more secure.
While the changes in the already established Blockchains (eg. Bitcoin) are hard to be made due to their extensive usage and a vast number of blocks.
We will definitely be seeing a massive change in the Blockchain Cryptography for all the new cryptocurrencies to come.
(Click Here to Learn About Proof of Attendance Protocol)
